Educate your Staff on the Importance of Cyber Security.
Barlop Business Systems helps small to mid-sized businesses (SMBs) thwart cyber attacks and protect their organizations from unnecessary downtime by addressing the most common tactic that cyber criminals use to attack modern workplaces; phishing. The overwhelming majority of security breaches caused by phishing are completely avoidable. While cyber criminals have grown more sophisticated in their approach, the average attack consists of the same key ingredients: an under-educated employee, effective bait and a temporary lapse in judgment. While we are in the business of securing an organization’s entire network and protecting them from any threats whatsoever, there are some initial steps that will safeguard a company without costing much time, energy or capital expenditure. These measures we’d like to share are extremely easy to implement and are excellent first steps in protecting a company from cyber crime. South Florida businesses can avoid the vast majority of cyber-attacks coming at their business. Below we discuss what are some of the simplest, yet most effective ways at minimizing risk within an organization.

“If all organizations were even this educated about cyber-attacks, we would see a dramatic drop in incidents”
What is a Phishing Attack?
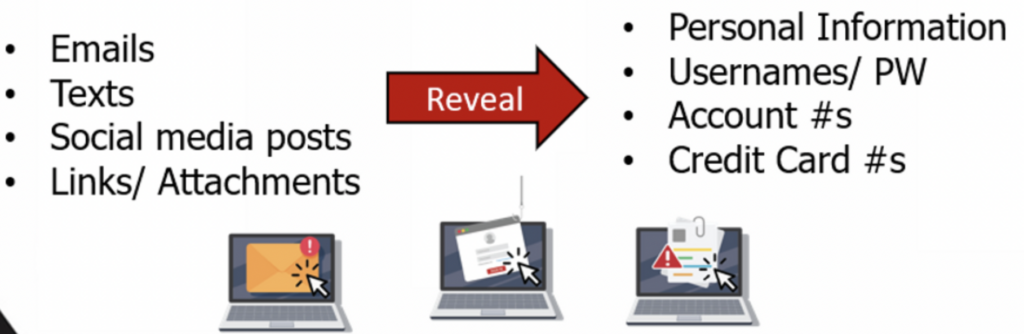
Phishing is the fraudulent practice of sending emails purporting to be from reputable companies in order to induce individuals to reveal personal information, such as passwords and credit card numbers, Social Security number, or login IDs, usernames, and passwords. Once obtained these credentials are obtained they use it to steal your money and/ or identity.
What does a phishing attack look like and what are the different types?
In a nutshell, phishing starts with fraudulent communication via email, text messages, or social media. A message appears to be from a trusted source like your bank, an e-commerce site, the IRS, Dropbox, your local public library, FedEx, or any number of others, but it isn’t.
Spear Phishing— Some phishing attacks are random. Spear phishing is more sophisticated and specifically targeted to certain groups, organizations, or people. After stealing credentials, criminals can wreak all sorts of havoc once inside your system.
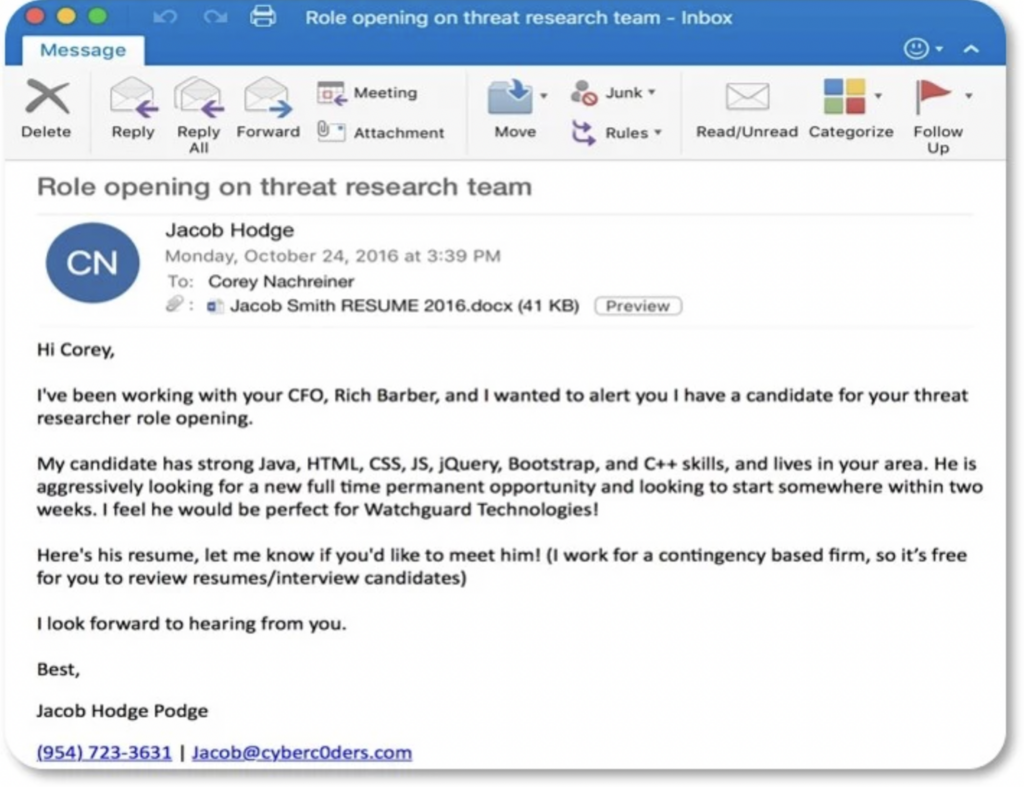
Spear-phishing example:
•Personalized to me
•Fits my job role
•Understands business relationships
•Sender makes sense in context
•Malicious attachment fits context
Old phishing example:
•Not individualized
•Bulk recipients
•Uses real assets
•Malicious document
CEO Fraud— This phishing scam targets employees within an organization by impersonating the company’s CEO email.
Social Media Phishing— Instead of using email or texts, these phishing scams use social media platforms. Phishers use this type of phishing to build trust with their targets before the attack happens. They make offers for goods or services, or promise rewards, like gift cards.
Mobile Phone Phishing— Phishers send messages via text messages or instant messaging platforms. The goal is to deceive people into giving away sensitive information that lets them access financial accounts or steal identities.
What is the purpose of a phishing attack?
The purpose of Phishing is to trick people into giving away sensitive information and/ or downloading malware to your server/network, therefore committing fraud and. or open your business and your customers up to attacks.
How to identify a phishing attack.
There are a few ways to identify a phishing attack. Urgent messages about your bank account, credit card, a friend who needs money, or a package you ordered are common phishing lures. See below for some common examples.
Bank account or credit card concerns
Google doc/ Dropbox/ file-sharing notification
FedEx/ UPS/ USPS shipping notification
What is a phishing email and how can one be recognized?
Unknown Sender The email address may be nonsense or have an incorrect format. In an Amazon spoof email, the address might be something like michelefd@amazon.org or something equally nonsensical.
Emotional Appeal Phishing emails frequently have an urgent tone.
Spelling/Grammatical Errors Many phishing emails have grammatical and spelling errors.
URL Link Hyperlinks (the links given in the message) which direct you to a different site
Solicits Sensitive Information Unlike legitimate companies, phishers ask you to send sensitive info via email or give links to a website for verifying your credentials.
How can Phishing be prevented?
Preventing phishing is simple for your company with Barlop’s Managed IT Services.
How do we protect the organization?

Effective Cyber Security with proactive defenses
Enable & empower reporting
Enable faster response
Neutralize threats
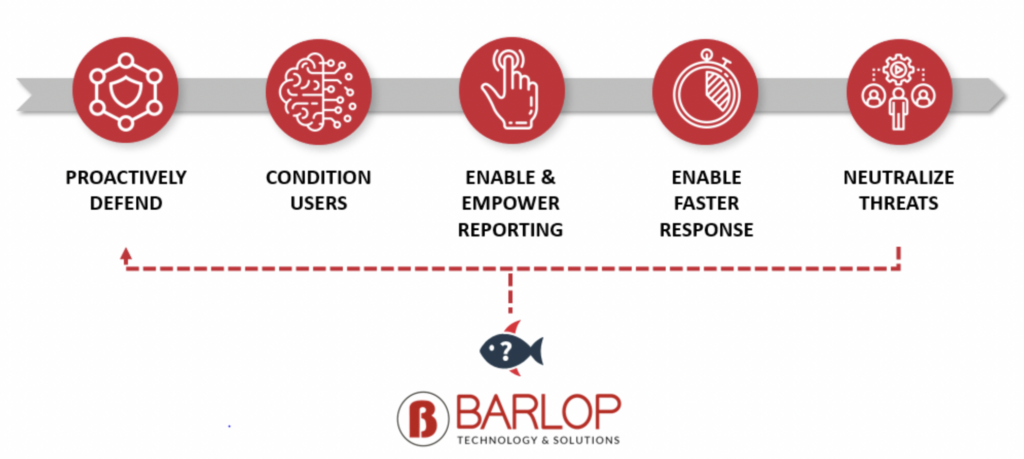
Preventing yourself and your company from being victimized by phishing attacks begins with awareness. It is important that everyone in your organization should learn how to recognize, report, and prevent phishing messages.
To protect your brand and clients, BTS’s monitoring service uses top of high-quality software and monitoring to protect your business. Our industry-leading take down times mean less risk to your business, less exposure for your customers, and less risk to intellectual property.
Learn more about Barlop’s Managed IT Services and Cyber Security today.